SSL certificate for Unifi controller in Synology docker container
I guess the topic perfectly describes what this post is about.
First and foremost, this whole blog idea is just a way for me to easily find this info again, in case I need it.
Secondly, hopefully this info helps you out too, in case you want to have a valid SSL certificate for your Unifi Controller. Which is running in a Docker container. On your Synology NAS.
The actual and useful info starts here.
Ok, first we need to establish a few facts/prerequisites.
- I’m running the latest jacobalberty/unifi image. These instructions might work with other images, just make sure the path to the keystore is correct.
- You need to install the Java8 package on your Synology. It contains the important keytool command. Without it, you can skip reading the rest of this post.
- I’m assuming you have acme.sh already installed on your Synology NAS. If not, check out this post.
- In this post I’m using unifi.domain.com as an example, replace it in code snippets and commands with your FQDN.
- The path to the keystore in my examples, /volume1/docker/Unifi/Data, is also an example and should be replaced with the correct path.
I have created a folder in File Station called “docker”, which contains various docker container paths. The Unifi container has mapped paths like this: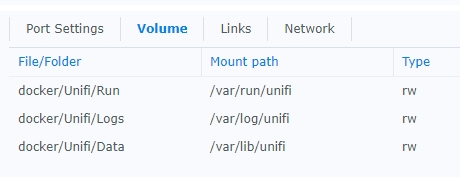
If you have all that, it’s time to enable the SSH service to your Synology NAS and start a root session (you can’t log in as root, you’ll have to login as an admin user and sudo su – to root).
Start by creating the following script.
Use your favorite text editor to create and edit /usr/local/share/acme.sh/unifi-renew-hook.sh, then enter the following:
#!/bin/bash
# Renew-hook for ACME / Let's encrypt
echo "** Configuring new Let's Encrypt certs"
cd /volume1/docker/Unifi/Data/
rm -f unifi.p12 unifi.key unifi.crt
openssl pkcs12 -export -in /usr/local/share/acme.sh/unifi.domain.com/unifi.domain.com.cer -inkey /usr/local/share/acme.sh/unifi.domain.com/unifi.domain.com.key -out unifi.p12 -name unifi -password pass:aircontrolenterprise
keytool -importkeystore -deststorepass aircontrolenterprise -destkeypass aircontrolenterprise -destkeystore keystore -srckeystore unifi.p12 -srcstoretype PKCS12 -srcstorepass aircontrolenterprise -alias unifi -noprompt
rm -f unifi.p12
echo "** Restarting container"
docker restart jacobalberty-unifi
Save and exit the text editor.
Run the command to issue the certificate for the first time.
The command below will request the first certificate and create a configuration file for acme.sh.
The –pre-hook command will run each time the certificate is renewed. In this case it will create a backup of the Unifi configuration backups and the keystore.
The acme.sh script saves the CSR, certificate and key files under /usr/local/share/acme.sh/unifi.domain.com/, so you can always retrieve them. The –fullchainpath and –keypath parameters copy the certificate and key files to the specified paths. We’re not using these files here, but they might come in handy some time.
acme.sh --force --issue --dns dns_cf -d unifi.domain.com --home /usr/local/share/acme.sh \
--pre-hook "tar zcvf /usr/local/share/acme.sh/UnifiKeySSL_`date +%Y-%m-%d_%H.%M.%S`.tar.gz /volume1/docker/Unifi/Data/backup /volume1/docker/Unifi/Data/keystore" \
--fullchainpath /volume1/docker/Unifi/Data/unifi.crt --keypath /volume1/docker/Unifi/Data/unifi.key \
--reloadcmd "sh /usr/local/share/acme.sh/unifi-renew-hook.sh" \
--dnssleep 20
Auto-renewing the certificate.
If you haven’t set this up yet, take a look at my previous post.
You only need 1 single Scheduled Task to update all Let’s Encrypt certificates on the same system.
You might want to disable the SSH service when you’re done.
That’s all there is to it.
Credits:
I got my inspiration from naschenweng.info‘s post about Securing Ubiquiti UniFi Cloud Key with Let’s Encrypt SSL.

